Healthcare organizations are increasingly migrating to the cloud. They are using public cloud services to host patient-facing apps, generate new clinical and operational insights, facilitate collaboration among healthcare teams, and store fast-growing volumes of health data.
Public clouds give organizations the flexibility to rapidly scale resources while avoiding large capital expenditures. At the same time, today’s leading public cloud providers can offer innovative technologies, such as artificial intelligence (AI) and analytics capabilities, which organizations can use to augment their services
No matter how your healthcare organization uses the cloud, maintaining HIPAA compliance must be a top priority. You need to ensure the privacy and security of protected health information (PHI), safeguarding it from theft, fraud, and other unauthorized use. And you must be able to prove HIPAA compliance to regulators as well as patients and healthcare partners, or risk extensive fines and damages to reputations.
While public cloud providers like Microsoft Azure offer guidance and resources for designing HIPAA-compliant environments, they do not do everything for you. When it comes to achieving HIPAA compliance in Azure, ultimately the responsibility falls with the organization. If you’re just getting started with Azure or you’re aiming to move business-critical healthcare workloads into production, there are a few “i’s” to dot and “t’s” to cross first. Here are four must-do’s for getting started with HIPAA compliance in Azure.
-
1. Understand the Shared Responsibility Model
Before you do anything else, make sure that everyone who will interact with your cloud environment has a clear understanding of the Infrastructure as a Service (IaaS) Shared Responsibility Model. For someone who has experience with cloud this may seem like a no-brainer, but for IT personnel who are still new to cloud, having this understanding will be critical for your Azure success.
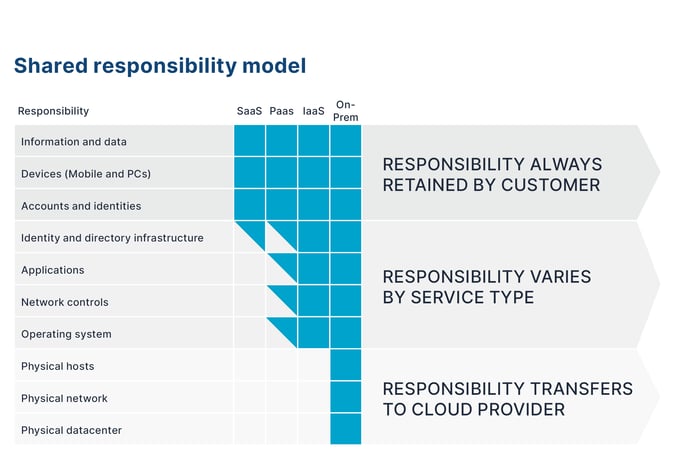
While in a traditional data center the organization owns security from end to end, from physical premises security to the network all the way to your applications and their data, in public clouds like Microsoft Azure the security responsibilities are shared between the customer and the cloud service provider. For example, Microsoft ensures that the physical infrastructure is secured by access controls on facilities such as locks, key cards, and video surveillance. It also ensures that the services it delivers are reliable and fault tolerant and able to failover to other geographical locations in the event of an outage. But the customer is responsible for securing the data he/she puts in the cloud. For example, enforcing complex password policies and enabling multi-factor authentication on access keys to ensure that hackers can’t easily break in.
One way to think of shared responsibility is to compare your cloud environment to a multi-tenant office building. In an office building, the owner of the building secures the front door with guards, video surveillance, and an access control list at the front desk. The owner ensures that the bathrooms and mailrooms are maintained and that only employees who work in the building have access. But each company that rents office space within the building is responsible for securing their own work environment. For example, the owner can’t help if a hacker steals an employees ID and keycard, gains access to his/her office, and steals a laptop.
-
2. Sign a Business Associate Agreement with Microsoft
Your account manager should mention this but I want to bring it up so it doesn’t get missed. Microsoft will sign a HIPAA Business Associate Agreement (BAA) with Microsoft Azure users that covers in-scope services. A BAA is a written contract between a covered entity and a business associate that describes how the business associate adheres to HIPAA along with the responsibilities and risks they take on. A BAA is required by law for HIPAA compliance.
While having a BAA in place is necessary for HIPAA compliance, it does not ensure compliance. As discussed previously, cloud HIPAA compliance ultimately depends on how cloud services are used, so the covered entity must still maintain responsibility for ensuring it’s cloud instances are configured correctly.
-
3. Use in scope services
Microsoft works rigorously to ensure that the services it delivers to clients are compliant with multiple regulations, such as HIPAA, ISO, and PCI. However not every Azure service is configured in scope with HIPAA requirements. To understand which Azure services can be used for protected health information (PHI) check the list of in scope services. For any service not on the list, you can still use it – just not for healthcare applications that interact with PHI.
-
4. Adopt Infrastructure as Code
Traditionally, configuring IT resources can be a slow, manual, error-prone process. Given the rapid pace of development that happens in the cloud, where spinning up new infrastructure is push-button easy for developers, this can often spell out “trouble” for security and compliance teams. Infrastructure as code (IaC) solves this problem by ensuring that each deployment is done the same way, the right way, and in alignment with your organization's policies.
In Microsoft Azure you can use the Azure Security and Compliance Blueprint for HIPAA/HITRUST to get started with IaC. The Blueprint specifies Azure resources for ingesting, storing, analyzing, and interacting with data as well as for manag-ing identity and security. It includes a sample use case scenario, a deployment template and automation scripts, a security threat model, a list of relevant HIPAA/HITRUST requirements, and more. Designed as a modular foundation, the Blueprint can be adjusted for an organization’s specific needs.
The Azure HIPAA/HITRUST Blueprint is an important resource for getting started. It can also serve as a means for evaluating compliance with environments that have already been established. For example, you can use the HIPAA/HITRUST Blueprint to determine whether you have sufficient processes and policies in place to comply with regulations.
Next Step: Implement Best Practices
While the four tips listed above are necessary for laying the foundation for HIPAA compliance in Azure at any organization, they will only get you started. After that you will need to codify and implement best practices to ensure your organization is keeping up with your end of the shared responsibility model.
To learn ten best practices for achieving HIPAA compliance on Microsoft Azure, download the full white paper today.

