As organizations store and manage more health information in cloud environments, their attack surface areas are expanding. They face a growing risk that their environment will be breached, leaving sensitive patient data exposed. In fact, the number of healthcare data breaches has more than tripled in the last ten years. Hackers are finding new ways to take advantage of weak security and access data.
How can your organization better protect healthcare data? Working toward HITRUST Common Security Framework (CSF) certification is one of the best paths toward fortifying your healthcare data security program. With HITRUST certification, you can reduce your risk profile while clearly demonstrating your strong cybersecurity position in the marketplace.
What is HITRUST Certification?
HITRUST certification is an accreditation program designed to help organizations demonstrate that their data security and privacy controls comply with rigorous security standards and regulations. Though HITRUST certification was initially developed for the healthcare industry, it is now used in a broad array of industries. In the healthcare sector, organizations use HITRUST to signal compliance with regulations such as HIPAA (the Health Insurance Portability and Accountability Act of 1996) and HITECH. Simply put, HITRUST certification is the gold standard for demonstrating regulatory compliance in healthcare.
The HITRUST organization offers three certification and assessment options:
- HITRUST Essentials 1-year (e1) Assessment: An entry-level validated assessment and certification.
- HITRUST Implemented, 1-year (i1) Assessment: An assessment that provides a moderate level of assurance that organizations have adequately addressed cybersecurity threats.
- HITRUST Risk-based, 2-year (r2) Assessment: The most rigorous assessment, with the most comprehensive set of control requirements. An interim assessment must be conducted every other year.
How Do You Get HITRUST Certified?
HITRUST certification is a comprehensive process that takes a risk-based approach to evaluating an organization’s security controls and practices. An external assessor helps identify the risks to security, determine the likelihood of a breach, evaluate the potential impact of a breach, and identify additional safeguards that could mitigate that impact.
To achieve certification, organizations ultimately must implement controls defined in the CSF. That framework covers a wide range of areas, including risk management, access control, network security, and incident management. Depending on which HITRUST certification and assessment option you choose, your organization might need to implement tens or hundreds of controls.
While implementing security is a critical part of the certification process, it is not the only part. Here are seven steps that your organization should follow if you are considering HITRUST certification:
1. Determine if HITRUST is right for you.
While complying with HIPAA is mandatory for healthcare organizations, HITRUST certification is voluntary. Nevertheless, a growing number of hospitals and other institutions require their partners and vendors to be HITRUST certified. Demonstrating compliance through HITRUST certification can help you improve competitive differentiation and win key contracts.
Just as important, working toward HITRUST certification can help your organization strengthen cybersecurity—and that is critical for all healthcare organizations that manage, store, or process sensitive data. The healthcare industry remains a primary target for cyberattacks. Attackers know that healthcare data—which can include names, addresses, social security numbers, and credit card numbers—is more valuable than any other type of data. They realize they can rake in huge sums by holding that data ransom, or by stealing it and then selling it on the black market.
The costs of failing to protect healthcare data are enormous and rising. According to IBM, the healthcare industry experiences the highest data breach costs of all industries. The average cost of a single data breach in healthcare reached $10.93 million in 2023. HITRUST certification can help you reduce the likelihood that you will be a victim.
2. Select a HITRUST assessor.
Once you decide to pursue HITRUST certification, you need to find a HITRUST assessor.
HITRUST assessors are third-party organizations that are authorized to conduct HITRUST assessments. An assessor evaluates an organization’s security controls and risk management practices against the requirements of the HITRUST CSF.
Choosing the right assessor is a critical decision, as the right assessor will be able to guide you through the process and simplify it as much as possible. Learn more about choosing a HITRUST assessor here.
Read the blog Seven Tips for Choosing a HITRUST Assessor
3. Conduct a readiness assessment and gap analysis.
The assessment process begins with a readiness assessment—a preliminary review of your organization’s security controls, policies, and procedures. The goal is to identify areas that need improvement before the actual HITRUST assessment. Your HITRUST assessor performs the readiness assessment. They will use the results to help develop a gap remediation plan.
4. Perform gap remediation.
The gap remediation plan identifies the specific areas where your organization needs to improve security controls and risk management practices to meet HITRUST CSF requirements. It also provides guidance on how to address these gaps, including recommendations for technical and administrative controls, policies, and procedures.
The gap remediation plan typically includes a timeline for completing the remediation activities, as well as responsibilities for each activity. The plan also includes a roadmap for testing and validating the effectiveness of the remediation efforts.
Once the gap remediation plan has been completed, your organization will need to implement the recommended controls and practices to address the identified gaps.
5. Conduct the validated HITRUST assessment.
After remediating gaps, your organization can begin the HITRUST validated assessment. The assessment is conducted by the HITRUST assessor and includes a review of your organization’s policies, procedures, and implementation.
Your team is responsible for providing evidence that demonstrates your organization is meeting the requirements of each HITRUST control in the assessment. Evidence is usually provided by screenshots and mappings to policies and procedures.
Typically several team members help provide that evidence—such as an IT manager, security manager, and privacy officer—but this can vary across different organizations. Other functional groups play a less time-consuming but essential role. For example, the HR manager could be tasked with providing evidence of HIPAA training.
The assessor also conducts interviews with key personnel to ensure they understand and follow policies and procedures.
6. Address any findings and complete the assessment.
If any issues are identified during the assessment, the assessor will provide a report outlining the findings and recommendations for remediation. Your organization would need to address any findings and provide evidence of remediation to the assessor.
Once the assessor is satisfied with your submission, you enter a 90-day “no change” period, where you’re not allowed to make any modifications to your control environment. Your assessor reviews and submits your work to the HITRUST Alliance for review and approval. You should receive your results back in one to three months.
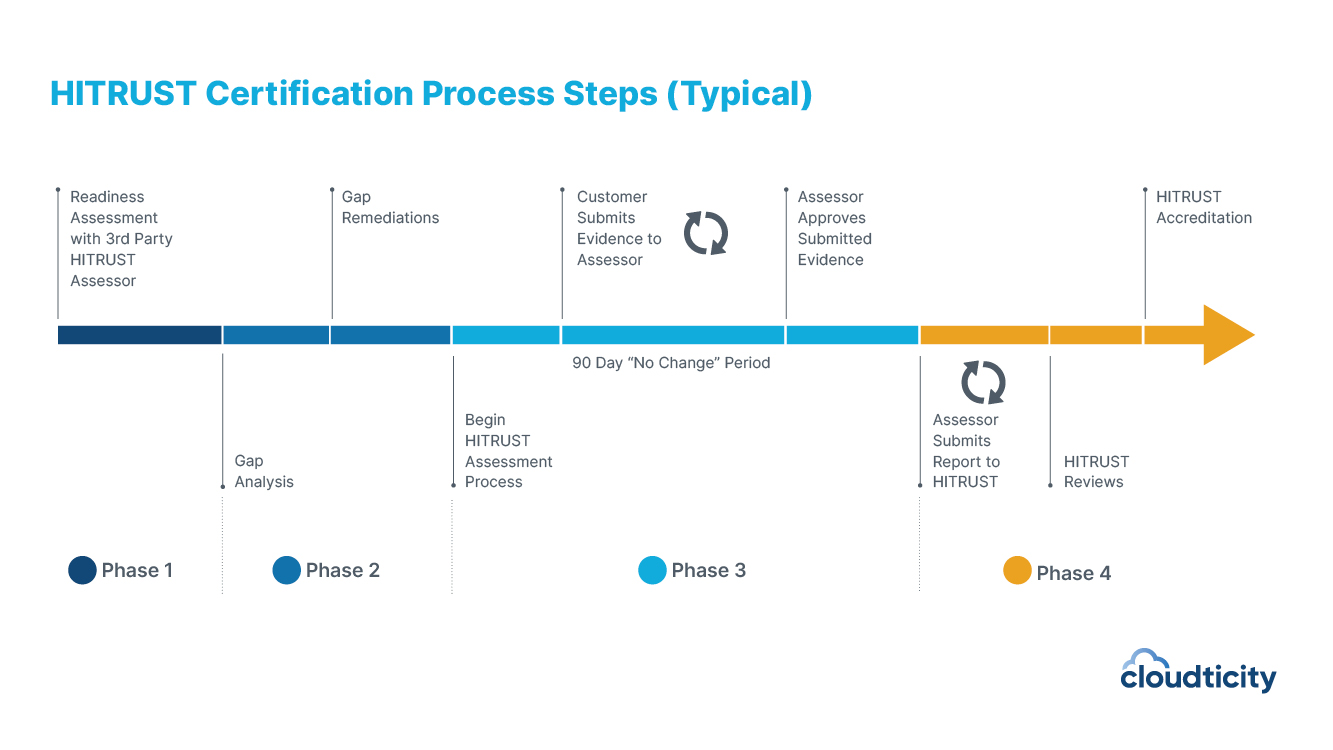
7. Maintain your HITRUST certification.
HITRUST certification is not a one-time event. If you choose the risk-based 2-year (r2) assessment, you will need to conduct an interim assessment every other year. If you choose one of the other assessments, you would need to run the assessment again every year.
How You Can Get Certified (and Recertified) Faster
If you want to get HITRUST CSF certified faster, using the right public cloud service provider (CSP) can help. Amazon Web Services (AWS), Microsoft Azure, and Google Cloud offer HITRUST certified services that allow you to inherit attestation to a number of control requirements they’ve already met. Inheriting controls can significantly reduce the work required for earning certification.
There are also a handful of CSP partners that offer HITRUST inheritance through their platforms. Cloudticity offers nearly 400 inheritable and partially inheritable controls. With Cloudticity, you can accelerate the certification process by 40–60% on average. Learn more, read about the HITRUST Inheritance Program.
Start Your HITRUST Certification Journey
Maintaining compliance with strict regulatory requirements in the healthcare industry is no easy feat. Demonstrating that compliance by undertaking the multi-step process of HITRUST certification might appear even more daunting. But HITRUST certification is well worth the effort. Achieving certification can help you bolster your organization’s security while providing an important point of competitive differentiation.
Learn how Cloudticity can help your organization accelerate HITRUST certification. Schedule a free consultation with a healthcare cloud expert today.

